


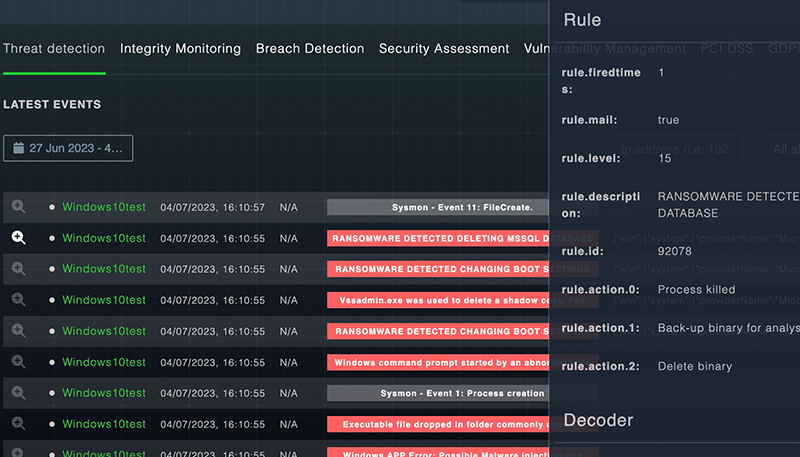
Semon agents diligently scan your systems, hunting for malware, rootkits, and suspicious anomalies. They reveal hidden files, identify stealthy processes, and detect unregistered network listeners. Moreover, they spot system response inconsistencies. Additionally, Semon's server component bolsters protection by using a signature-based intrusion detection method. It scrutinizes log data for malicious activity patterns, swiftly identifying potential threats to ensure no attacker goes unnoticed.
Semon integrates with popular providers like AWS, Azure, and Google Cloud. It uses predefined rules for effortless vulnerability detection. Moreover, Semon's versatile, multi-platform agents are invaluable for instance-level cloud monitoring, ensuring robust security.
Semon boosts Docker security by tracking hosts and containers for threats. It integrates seamlessly with Kubernetes, providing deep insights into images, volumes, and active containers. Its robust features help you proactively mitigate risks, ensuring cluster integrity.
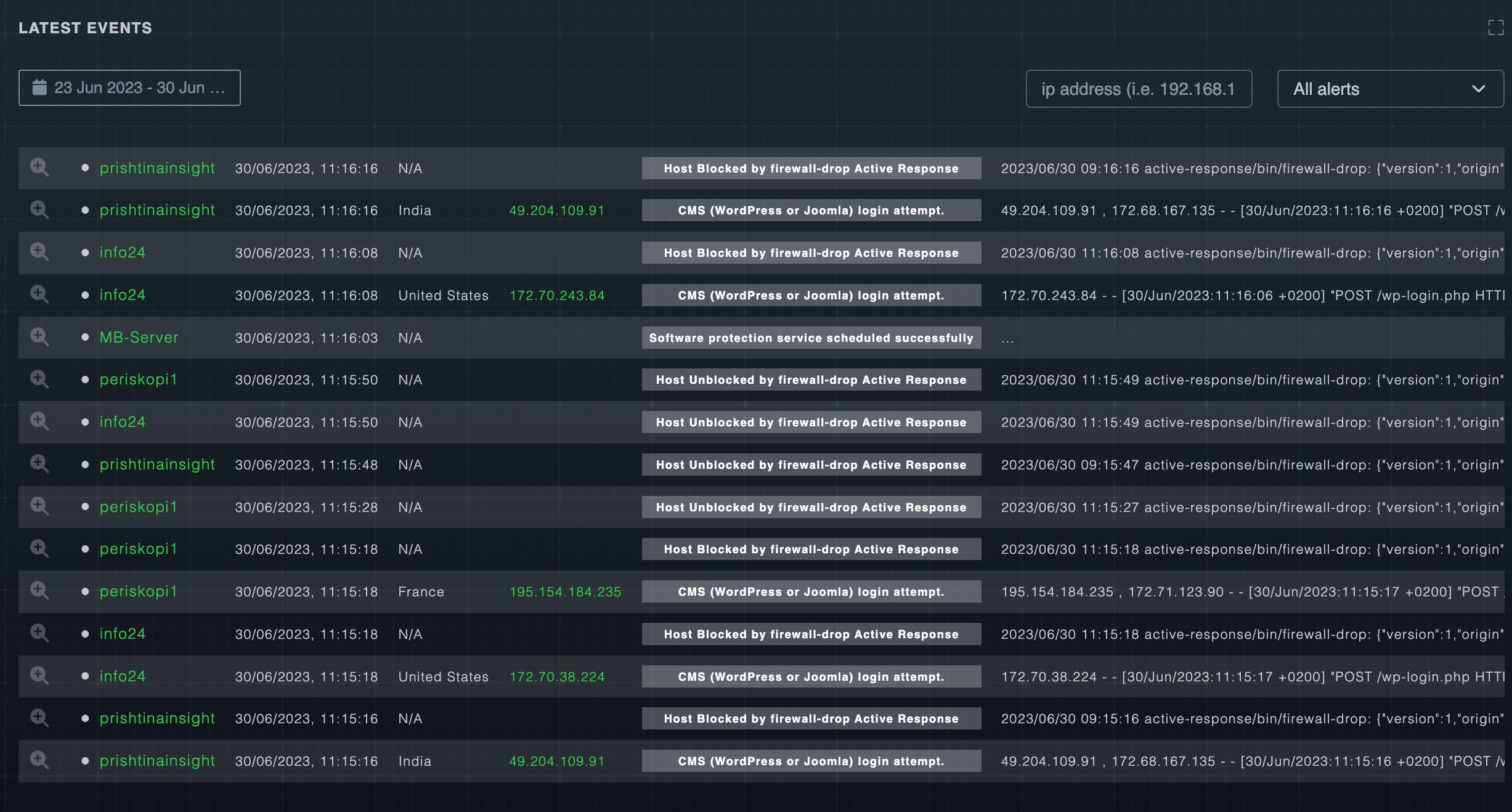
Semon methodically collect and analyze system and cloud logs such as AWS CloudTrail or Log Analytics in Azure, alerting to errors, misconfigurations, and threats. If agents aren't present, the server still gathers data. With Semon, you're always prepared for potential issues.
Semon diligently oversees your file system, continuously monitoring for any alterations in content, permissions, ownership, and file attributes that demand your attention. Furthermore, Semon possesses the inherent ability to accurately identify the users and applications responsible for file creation or modification, providing comprehensive insights into the actions taking place within your system.
The file integrity monitoring capabilities of Semon prove invaluable when combined with threat intelligence, allowing you to swiftly detect potential threats or compromised hosts. Moreover, several regulatory compliance standards, including the stringent PCI DSS, recognize the significance of file integrity monitoring and explicitly mandate its implementation. By leveraging Semon's capabilities, you not only bolster your security measures but also ensure adherence to critical regulatory requirements, thus safeguarding your organization's reputation and maintaining compliance with industry standards.
Semon agents retrieve software inventory data and transmit it to the server, where it is cross-referenced with up-to-date CVE (Common Vulnerabilities and Exposure) databases. This meticulous process allows for the identification of well-known vulnerable software within your infrastructure.
By employing automated vulnerability assessment, you gain the ability to pinpoint weak points in your critical assets proactively. This proactive approach enables you to take corrective measures before malicious actors have a chance to exploit vulnerabilities, safeguarding your business operations and protecting sensitive data from potential sabotage or theft.
Semon diligently oversees system and application configuration settings, ensuring compliance with your organization's security policies, standards, and hardening guidelines. Its agents conduct regular scans to identify any vulnerable, unpatched, or insecurely configured applications.
Moreover, Semon provides the flexibility to customize configuration checks, tailoring them specifically to align with your organization's unique requirements. In the event of non-compliant configurations, alerts are generated, accompanied by recommendations for improved configuration, references, and mapping with relevant regulatory compliance standards. This comprehensive approach ensures that your systems are configured optimally, promoting enhanced security and adherence to industry regulations.
XDR is an extended detection and response solution that goes beyond typical endpoint detection. It collects and automatically correlates data across multiple security layers - endpoint, network, cloud, and more - for improved threat detection and response.
Unlike traditional EDR solutions that focus only on endpoints, our XDR solution provides a more holistic view by integrating data from numerous security layers. This results in a more comprehensive and effective approach to detecting and responding to threats.
Our XDR solution is designed to detect a wide range of threats, from malware and ransomware to more sophisticated, advanced persistent threats (APTs). By integrating data from multiple sources, it can detect threats that might be missed by other security solutions.
Our XDR solution not only detects threats but also responds automatically to mitigate them. This can include isolating affected systems, blocking malicious activity, and providing detailed information to security teams for further investigation.
Yes, our XDR solution can be integrated with various security tools to enhance its effectiveness. It's designed to work seamlessly with your existing security infrastructure, improving visibility and control.
Organizations of all sizes and in all sectors can benefit from our XDR solution. Whether you're a small business with limited IT resources or a large enterprise facing sophisticated threats, our XDR solution can help improve your security posture.